2/20/2015

source

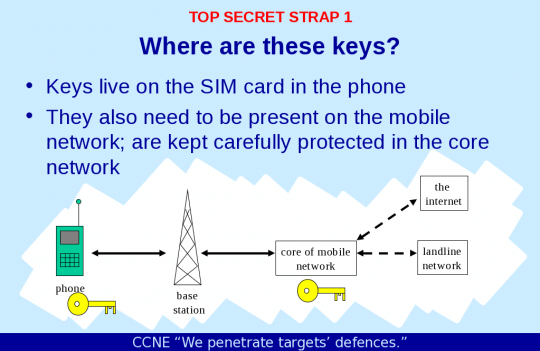
The American National Security Agency (NSA), and the British Government Communications Headquarters (GCHQ), similar clandestine intelligence agencies, stole SIM card encryption keys from a manufacturer, allowing the groups to decrypt global cellular communications data.
The effort, according to The Intercept, took place in 2010, with the agencies breaking into a Dutch firm, Gemalto. The hack provides the government agencies the capability to monitor “a large portion of the world’s cellular communications,” according to the report. We are of course supposing that the government’s descriptions of its own capabilities are accurate.
Update: Gemalto said it is investigating the issue and is not immediately able to confirm the report. You can find its full statement at the bottom of this post.
(Gemalto most recently turned up in the technology media as a partner in a new product of Box, a cloud storage and enterprise collaboration provider, designed to bring added encryption to its customers. Box declined to comment on the new matter.)
The Intercept’s reporting is, once again, based on documents released by former NSA contractor Edward Snowden. The firestorm initially ignited by Snowden has dimmed in the past year, waning as the pace of revelations sourced from the information he released has slowed.
The NSA and the GCHQ formed the Mobile Handset Exploitation Team (MHET), according to the report, which was built to do precisely what it’s name suggests.
“This disclosure is incredibly significant,” The Electronic Frontier Foundations’ Mark Rumold told TechCrunch. “NSA and GCHQ basically have the keys to decyrpting mobile communications anywhere in the world, even without the participation of local communication carriers (which, even if not much, acts as some check on intelligence agency behavior). It’s the equivalent of these agencies having printed doorkeys for the front doors to millions or even billions of homes around the world, just in case they one day decided they needed to get in. Frankly, people should have no faith in the security of global mobile communications.”

NSA Slide describing the keys that it compromised.
Today’s revelations harken back to the earlier days of the Snowden saga, when theXKeyscore program was still a cause célèbre among the tech industry: The NSA and the GCHQ managed to infiltrate Gemalto by tracking the communications of its employees, using XKeyscore as their data collection tool of choice, according to The Intercept.
So what was unveiled today is built on the tools that privacy advocates worried would be abused when they were first detailed. The use of presumably innocent peoples’ private communications data to lift the encryption keys of other individuals is precisely the sort of overreach that agencies operating in the dark are suspected of abusing.
We have reached out to the NSA and GCHQ for comment but have not heard back. However, the ACLU’s Christopher Soghoian tweeted about the irony of the matter earlier:
The Dutch Members of Parliament has demanded a response from both organizations over the alleged attacks:
When asked if there were other groups targeted besides Gemalto, Glenn Greenwald responded in an email to TechCrunch that, “In general, we can’t really comment on things that haven’t yet been reported.”
Standing by itself, that the NSA would break into a private corporation to steal individual encryption key might seem shocking. However, recall that the NSA was more than content to tap the cables that linked private data centers of American technology companies located abroad. That particular program led to firms like Yahoo and Googlegreatly increasing their use of encryption in its various forms.
Today the NSA and its British cohort have again been shown to have less than minor respect for private property, or privacy.
Also, today’s release indicates that there might be more revelations of NSA activity coming. That fact is worth keeping in mind, as we are racing towards a showdown in Congress over renewing several parts of the Patriot Act — which provides key legal underpinning for parts of NSA surveillance — that are set to automatically sunset. So, there will soon be another national debate about surveillance and privacy. Stories such as today’s report concerning SIM cards, and the integrity of the encryption and data privacy of global citizens will certainly help set that discussion’s tone.
Update: Gemalto has released a statement in which it said that it is unable to corroborate the report at this point, but it intends to investigate the issue:
A publication reported yesterday that in 2010 and 2011, a joint unit composed of operatives from the British GCHQ (Government Communications Headquarters) and the American NSA (National Security Agency) hacked SIM card encryption keys engraved in Gemalto and possibly other SIM vendors’ cards. The publication indicates the target was not Gemalto per se – it was an attempt to try and cast the widest net possible to reach as many mobile phones as possible, with the aim to monitor mobile communications without mobile network operators and users consent. We cannot at this early stage verify the findings of the publication and had no prior knowledge that these agencies were conducting this operation.Gemalto, the world leader in digital security, is especially vigilant against malicious hackers, and has detected, logged and mitigated many types of attempts over the years. At present we cannot prove a link between those past attempts and what was reported yesterday.We take this publication very seriously and will devote all resources necessary to fully investigate and understand the scope of
sophisticated techniques.There have been many reported state sponsored attacks as of late, that all have gained attention both in the media and amongst businesses, this truly emphasizes how serious cyber security is in this day and age.
source
No comments:
Post a Comment